Posts Tagged ‘Information Security’
Friday, December 17th, 2010
 10 Tips to Help Keep Your Data Protected 10 Tips to Help Keep Your Data Protected
Hey everyone I’m Dustin, welcome back to our blog.
Worried about your information going out across the World Wide Web, continue reading to learn how you can get protected against loss of data, data theft, and data corruption.
- Physical Protection: Passwords, firewalls, and virus scanning are great but please don’t forget the basics. Keep your computer physically locked up or only leave it where you know for a fact that it will be safe. Even people you know can access your computer and bring unwanted problems if you give them the chance. Devices like security cables and alarms can be used but are not full proof. Making a note of the computer’s serial number can also be helpful if a theft does occur and needs to be reported. (Computer Protection Devices)
- Don’t be naïve not everyone is nice: Don’t give out your personal information to people you don’t know, it’s not a normal for strangers to ask for your address or birthday when you first meet them. Don’t provide too much information to social networking sites.
- Use Antivirus and Spyware programs: Using good Antivirus software is not enough anymore. New malicious programs are created and discovered every day so it is important that you not only have Antivirus software but that you keep it up to date as well. Antivirus programs scan, track, and remove any problems from your hard drive. Like Antivirus software a spyware program can detect and eliminate any spyware that has made a home on your hard drive. Many Antivirus programs do have anti-Spyware included, if yours does not, you will need to install a separate program for Spyware. Spyware can often track your web usage, violate your privacy, add unwanted features, and take up your computer usage for its own purpose. (Learn More)
- Back up your information: If you don’t already have a back up of your hard drive you should create one. Sooner or later you may encounter a problem that requires a complete hard drive wipe so avoid the hassle of re-building your information and create a backup. There are many programs that will automatically create a back up for you some of them programs include Symantec Backup Exec, Ace Backup, Nero Back it up, Save Me PC, and Evault. Chances are that if you have a security or antivirus program on your computer they will establish a hard drive back up already on a routine basis.
- Activate your Firewall: To make certain that your firewall (in Windows) is active access the control panel, go to network and connections, and select firewall settings. Additional programs like Norton Security Suite and McAfee Security provide additional firewall settings. A firewall acts as a barrier between the internet and your computer protecting it from outside access and intrusive problems. Firewalls are essential to controlling the traffic through the various network ports.
- Learn and Beware: Educate yourself, don’t be fooled, and take a closer look to see what information is accurate and safe. Avoid pop-ups asking you to install software, only install free software that you are sure about and no is safe. Don’t open attachments without scanning first and don’t open links in your emails that you suspect might be bogus.
- Avoid Phishing: Phishing is when emails falsely claim to be an existing organization that you do business with. These emails redirect a user to a website created to look like the legitimate site and then users are asked to update their personal information. Mean while the real company has no need of asking for updated information and you just supplied it all to a criminal. Be cautious of emails expressing urgency and avoid links and submission forms asking for financial information. Sensitive information like this should only be communicated using a secure webpage. (More about protecting yourself against phishing!)
- Make sure pages are secure: Whether it is to purchase items, check bank accounts, or to logon to other sensitive information be certain that site is displaying a security icon on the browser window. In addition to the locked icon, an encrypted web site URL will include https instead of the unencrypted http. Depending on the web browser that you are using the icon will be located in various locations. Take the time to familiarize yourself, knowing where yours is located could prove to be very beneficial. If using Internet Explorer the icon is located next to the search dialogue box at the top right and in Mozilla Firefox it is located in the lower left hand page border. Clicking this icon will launch a separate window detailing the security properties of the webpage. (How to tell if the Page is Secure)
- Create strong passwords: A password should be easy for you to remember and hard for others to figure out. A strong password should be 10 to 14 characters in length. The longer the better but only if you’re able to remember it. Avoid any password based on repetition, dictionary words, letter or number sequences, usernames, relative or pet names, romantic links (current or past), or biographical information (e.g., dates, ID numbers, ancestors names or dates). A password should include numbers, and symbols if allowed by the system. If the system recognizes case, use both capital and lower-case letters. On another note about passwords don’t leave them out where people can see them. A strong password is nothing if you leave a hard copy of it under the keyboard, taped to the desk, or even worst attached to the monitor. Hard copies should be kept in a digital wallet or safe. Also switch it up don’t use the same password for everything. If someone can get into your email that is bad enough you don’t want to give them access to your bank information also. An addition authentication tip is to confirm your user account does not have administrative access on your computer. If for example you are a regular user and despite having anti-Malware software installed, some malicious software gets through, the malware software would only be able to affect your profile and not your computer’s operating system as regular users cannot install most software. (How to Create and Strong Password)
- Wi-Fi Settings: When using public or personal Wi-Fi, be sure to turn off file sharing (Windows) by going to your control panel, selecting network and connection, tab to advanced settings and adjust accordingly. In addition you can activate privacy settings and change the firewall configurations in the same location. Make sure that you have an active firewall and ensure that you turn off the Wi-Fi when no longer using it. It’s also worth mentioning that users should always have their home Wi-Fi connections encrypted so users can’t stand around your house and access it. Also make sure no one is hovering to get your login password.
Hope these tips can help! It is only by taking preventative measures like these that we are able to hopefully stay ahead of cyber crime.
Keep your information Safe and Have a Great Day!
Dustin
ComputerFitness.com
Providing Tech Support to Businesses in Maryland

Tags: Firewall, Information Security, Software, strong password
Posted in Information Security, Mac and PC, PC, PC Maintenance | No Comments »
Friday, October 29th, 2010
 Hey, everyone, Josh from Computer Fitness back with another award-winning article to help you with your computer conundrums. Hey, everyone, Josh from Computer Fitness back with another award-winning article to help you with your computer conundrums.
Recently, another glitch in the iPhone’s security was found. When you lock the screen, there is a chance for people to gain access to your system, despite having a lock in place. It involves using the Emergency Call function, and a few quick button presses. This is concerning for many people, and Apple has yet to address it. There are rumors that it will be fixed in the upcoming software update, 4.2, but we aren’t sure yet.
Keeping your mobile device safe is important. The amount of data on it is vital to your business, personal life, or both. This is why proper security measures are so important. No matter which device you use, always password protect them. Whether it is a PIN or a 32 Digit masterpiece of a lock, make sure you take the right steps.
Tied into this is keeping passwords up to date and changing them as necessary. For example, if you set up your iPhone for SSH, which allows file transfers, etc., then you want to change the default password from “alpine” to whatever else. The same goes for routers and wireless networks. Always setup encryption, no matter how simple. A WEP goes a long way to keep people from stealing your data on your home wireless network.
Remember, you’re the best line of defense against digital attackers. You don’t have to be a specialist, but you do need to take the initiative.
Josh

Tags: Apple, Information Security, microsoft, Networking, passwords
Posted in Information Security | No Comments »
Friday, October 22nd, 2010
 Hey, everyone, Josh from Computer Fitness back with another award-winning article to help you with your computer conundrums. Hey, everyone, Josh from Computer Fitness back with another award-winning article to help you with your computer conundrums.
PC Backups are an important part of computer ownership. Just keeping a copy of your files is a great start. However, there are often programs that get left behind if you only save your media. Software backups vary as to what they offer, but an invaluable tool is PC Imaging software.
Think of this like a camera. The software will take a “picture” or image, on your machine, which you can use later. The image, in this case, contains everything on your computer at that point. Later, if you need to restore your PC’s files to another machine, you can practically pick up from where you left off.
Another valuable use of this technology is to create a template for new machines. If you run a small to medium sized business, odds are that you use similar or identical PCs in your office. In this case, your IT folks can configure the machines are necessary using a singular image file. This makes turn around much faster on broken machines.
Some software solutions to help you out with this are Norton Ghost for PCs and Time Machine for Mac OS X. Time Machine is included with all Macs made since 2008.
-Josh
Computer Fitness

Tags: backups, Information Security, Software, Tips, tools
Posted in Mac and PC | No Comments »
Friday, October 8th, 2010
 Hey, everyone, Josh from Computer Fitness back with another award-winning article to help you with your computer conundrums. Hey, everyone, Josh from Computer Fitness back with another award-winning article to help you with your computer conundrums.
Cyber criminals are out there; there´s no denying it. More and more we hear about attacks in the US or abroad against networks, companies, and governments. This is the same as it ever was, people trying to take from others. The methodology has changed and that is what we´re going to talk about today. One of the more common ways that attackers will go after a network is a DDoS, or Distributed Denial of Service.
When you contact a website, send an email, etc. You are exchanging data. That´s how this whole thing works. Various pieces of hardware route the data and make sure it gets divided up and sent to the right places. Now, have you ever seen a website that was “just taking forever today”? That´s an example of too much traffic being funneled through too small of an area. What a DDoS does, is a play on this weakness and flood the target with traffic.
Now, rather than some of the other methods of attack where a single user is the culprit, DDoS relies on hundreds of thousands of machines all forcing their way in at once. This leaves the routers et al. with far too much traffic to handle and they crash under the weight; the attackers now have what they want, a denial of service to anyone who uses the site.
Further reading:
-Josh
ComputerFitness.com

Tags: Attackers, DDoS, denial, Hackers, Information Security, internet, traffic
Posted in Internet | No Comments »
Friday, September 10th, 2010
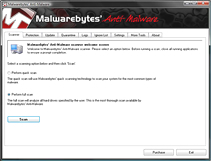 Malwarebytes Home Screen Hey, everyone, Josh from Computer Fitness back with another award-winning article to help you with your computer woes.
Malware is a real problem on the Web. The US is especially targeted, though malware is a global problem. In case you hadn’t guessed, malware is software designed with a malicious purpose. It could be just to harass you, but it could also be to steal precious data, like credit card numbers, from your PC without your knowledge. There are several options when choosing how to protect your computer. Here is one: Malwarebytes Anti-Malware. (MBAM)
Malwarebytes is a piece of software that can complement an anti-virus program well. MBAM scan for a lot of things that other software might miss. There are three levels of scanning that you can use as needed. I recommend a full scan once a month, and a quick scan once a week. The quick scans usually run between 10-30 minutes, so they can be used just about any time.
There are several benefits to choosing MBAM for your malware protection. First, it’s free. Now, you want to be careful when downloading free software from some random place on the Internet. In this case, I’ve done some research and used it personally with no ill effects. I cannot guarantee the same to you, as that would be irresponsible, but I have had a very positive experience. Next, it’s easy to use.
It may look complicated, but MBAM handles a lot of the heavy lifting for you. All you need to do is update it and tell it when to scan. If you don’t want to handle the rest, you don’t have to do so. Lastly, MBAM will catch problems that others won’t. I’ve been on several clients’ computers and MBAM has turned up things that their Anti-Virus didn’t.
You can download MBAM for free, or buy a full version with more features.
-Josh
Computer Fitness

Tags: computer, Information Security, Malware, mbam, protection, Software
Posted in PC Maintenance, Software | 2 Comments »
Wednesday, September 1st, 2010
 Hey, everyone, welcome back to the Computer Fitness blog! Hey, everyone, welcome back to the Computer Fitness blog!
Keeping your data safe and secure is a necessity in any business. Clients don’t want their private information being leaked all over the world, and who can blame them? We all want to make sure our privacy is protected at work and at home. Well, there are a lot of ways to ensure that you remain safe on the web. Today, we’re going to talk about one of them: Firewalls.
Picture a wall in your head. Now cover it in fire. That’s effective imagery, right? You wouldn’t be able to go anywhere near it. That’s the aim of firewalls on computers. They act as barriers to prevent people from just coming in and getting what they want. They are meant to establish lines so thick that nothing can penetrate them.
Getting a firewall is easy. All Windows and Mac operating systems have them built- in. They are also usually enabled by default. This is good because it keeps you from having to configure this yourself. They automatically block most ports you won’t use, and keep open ones that you will. A good example is port 80, which is the default for web browsing. That will be open, while others will not.
There are other forms of firewalls you can employ, and all have varying degrees of strength and customizability. For a home user, any good Anti-Virus bundle will include a more powerful firewall that is better equipped to handle your PC’s security.
-Josh
Computer Fitness

Tags: Firewall, Information Security, mac, pc, WWW
Posted in Firewall, Information Security | No Comments »
Thursday, August 12th, 2010
 Hey, everyone, Josh from Computer Fitness yet again. We are a Tech Support Company for Small and Medium businesses located in Reisterstown, MD. Hey, everyone, Josh from Computer Fitness yet again. We are a Tech Support Company for Small and Medium businesses located in Reisterstown, MD.
Protecting your PC is an important part of ownership. Just as you would buy a security system for your car, you must also acquire security for your computer. There are a plethora of options out there. You can choose from open source free programs to powerhouse software created by giant corporations. The latter is probably your best option if you don’t feel like spending hours learning how to use the software.
Symantec
Probably one of the best known protection suites, Symantec’s Norton Internet Security suite has been a household name for a while. It provides protection for up to 3 PC’s per household and covers a lot of areas. The reason I recommend this over the cheaper, Antivirus Edition, is because there are more than just viruses seeking to cripple your PC. On top of this, features like cloud-based definitions for threats and child protection while online are worth having.
McAfee
McAfee has been around for a while, too, and so they also have a respectable history. Their product is very similar to Symantec, and even Trend Micro. Features such as antivirus defense, firewalls, etc. are all present here. The biggest difference here is the lack of home network protection. This is included, in some form or another, in both Symantec and Trend Micro. Its absence here is notable.
Trend Micro
Trend Micro is, in my opinion, the best option out there today. While sporting similar features to its competition, Trend Micro stands out for its offer of 2GB of free online storage, quick scan times, and real time change tracking. These last options informs you the second attempt are made to change something on your PC. This is handy when installing programs and making sure they do what they say they will. On top of all this is an interface that is easy to use.
-Josh
Computer Fitness

Tags: Antimalware, Antivirus, Information Security, Malware, pc, Spyware
Posted in Information Security | No Comments »
Thursday, April 22nd, 2010
 Hello and welcome to Computer Fitness’ Blog! My name is Josh. You may know me from the Internet Beacon. We have a pretty cool blog over there. If you’re new to our sites, do check it out; there’s plenty more awesome over there. Computer Fitness is a tech support firm in Finksburg, MD. Our areas of expertise run the gamut from desktop repair to server maintenance. Hello and welcome to Computer Fitness’ Blog! My name is Josh. You may know me from the Internet Beacon. We have a pretty cool blog over there. If you’re new to our sites, do check it out; there’s plenty more awesome over there. Computer Fitness is a tech support firm in Finksburg, MD. Our areas of expertise run the gamut from desktop repair to server maintenance.
Windows User Account Control, or UAC, was introduced in Windows Vista as a way to make the Windows OS more secure. There are a lot of arguments as to whether or not this is true, but the fact remains that it is a part of Windows. Today, let’s examine some of the Pros and Cons of using UAC.
Pro – UAC Prevents Unauthorized Installations and Changes to Your System
UAC does its job here. It will keep changes from happening to your system without your express permission. This includes changing settings on your machine as well as installing software. This is incredibly handy, as a lot of malware gets around computers this way.
Pro – Adjustable Levels of Access
UAC allows you to set varying levels of warning for your computer. This comes in handy if you are always installing new programs or making changes to your PC. You can custom tailor notifications from the UAC in the Control Panel.
Cons – UAC Can Be Intrusive
One of the biggest complaints that users have about UAC is that it can be incredibly intrusive. This was more of a complaint in Windows Vista, but it is valid. Most people don’t know how to change the settings that control UAC, so getting a notification every time you want to do a lot of things on your PC can be very frustrating.
Cons – Too Specific
UAC’s biggest flaw is that it is too granular. The specificity that UAC applies to computer management is more of a hassle than a help. You can unblock one application but a process started by that application may be flagged. This leads to a lot of frustration and unnecessary action on the user’s part when dealing with UAC.
That about wraps up our section on Windows UAC. There is a lot more to this feature and I encourage you to check out more for yourself (see Windows UAC).
-Josh
Computer Fitness
Onsite and Remote Tech Support

Tags: Information Security, Tips, UAC, Windows
Posted in Desktop - Workstation | 1 Comment »
|
 10 Tips to Help Keep Your Data Protected
10 Tips to Help Keep Your Data Protected





 Hey, everyone, Josh from
Hey, everyone, Josh from  Hey, everyone, Josh from
Hey, everyone, Josh from 
 Hey, everyone, welcome back to the
Hey, everyone, welcome back to the  Hey, everyone, Josh from Computer Fitness yet again. We are a Tech Support Company for Small and Medium businesses located in
Hey, everyone, Josh from Computer Fitness yet again. We are a Tech Support Company for Small and Medium businesses located in 


