Archive for the ‘Information Security’ Category
Description of ‘Information Security’ Category: Posts about computer information security, which is protecting information and information systems from unauthorized: access, use, disclosure, disruption, modification, perusal, inspection, recording or destruction.
Friday, May 6th, 2011
As helpful as technology may be to businesses it can also present certain challenges. If poorly managed, business technology can often prove to be just as harmful as it is beneficial. This is why we have IT professionals or IT departments. Regardless of how much equipment a company may have the role of an IT department is a full time job especially when you consider the possible strain most companies place on their technology and their need to prevent any malfunctions.

Whether it is a single computer and printer or ten networked computers running off of a server it is mostly the IT department that handles the purchasing, installation, updating, management, and repair of company technology. In order for an IT department to be successful and maintain the integrity of the technology it should possess the following characteristics.
- Qualified and motivated staff
- Appropriate IT resources
- Effective department management
- Proper IT procedures
- Regular meeting, documentation, and review
It is the goal of an IT department to not only fix and manage the company equipment but to also ensure the security of information. To do so an IT department should be performing routine tasks, that includes establishing policies and procedures, updating equipment, and running diagnostics. The majority of work done by these departments should be preventive measures so that when problems do arise they already have procedures in place that detail immediate solutions. Now of course most IT departments cannot predict every incident that has the can occur however they should come pretty close to being able to recognize the most frequent or detrimental threats. Various simple but overlooked tips for a company and IT departments include,
- Password Policies, many users choose to utilize a password that is easy to remember rather than one that is sufficient to protect critical information. A company or IT department should implement a password policy that details and enforces the use of Strong passwords.
- Remote Access Policies, because many company employees need to be able to access company information from home or when traveling, a proper remote access policy should be drafted according to the specifications set by the IT department.
- Appropriate Use Policies, detail what resources should be used and how to use them appropriately. Having an acceptable use policy, whether it is for the use of the equipment, email, or the Internet can potentially prevent equipment errors and system vulnerabilities.
- Scheduled Backups, performing regular backup’s archives important information. In the event something does happen and wipes out your information you will still have the latest archived data to restore.
- Scheduled Updates, establishing automatic updates or routinely checking for software updates manually keeps software like anti-virus, anti-spyware, and firewall protection working properly and aware of the latest security threats.
- Routine System Checks, by running diagnostic tests you can see how your system is performing, document, and perform any necessary adjustments.
- Equipment Checks, similar to routine system checks this entails testing the equipment and making sure it is performing properly.
- Proper Training, to prevent the misuse of equipment all employees should be trained and well informed of the appropriate and inappropriate uses.
- Think Proactive, one the biggest errors when is comes to IT is waiting till something happens. It is most important that you don’t wait till it is too late to create the policies, implement the procedures and protect your technology.
It is extremely important that these bare minimum IT requirements be utilized in order to protect your business’s information and equipment. Even if your company does not have an IT department, you yourself should be implementing some of these suggestions or hiring an IT professional to assist you in protecting your technology. Don’t wait until an IT disaster strikes before you take the appropriate actions.
Is your IT department doing their job? What do you think is the most important element for managing your IT?
Thanks for Reading and Have a Great Day!
Dustin
ComputerFitness.com
Providing Tech Support for Businesses in Maryland

Tags: computer, equipment, Information Technology, IT, IT department, Maintenance, small business, technology
Posted in Information Security, PC Maintenance | No Comments »
Thursday, April 28th, 2011
On Friday April 22, 2011 the Sony PlayStation Network stated that as of April 19 th they had become aware that PlayStation and Qriocity user accounts had been hacked. Prior to this notification they have made several announcements, none of which providing the exact details for the disruption in network services.
During the time leading up to the official  public disclosure Sony had disabled their system which left many PlayStation Network users in the dark about the true circumstances surrounding the event. It wasn’t until April 26, 2011 that Sony offered the full explanation that user account information and potentially their financial information had been unlawfully acquired during an intrusion. The unauthorized intrusion of the network accounts left over 70 million users as well as their personal and financial information at risk. For a full timeline visit PlayStation Network Hack Timeline. public disclosure Sony had disabled their system which left many PlayStation Network users in the dark about the true circumstances surrounding the event. It wasn’t until April 26, 2011 that Sony offered the full explanation that user account information and potentially their financial information had been unlawfully acquired during an intrusion. The unauthorized intrusion of the network accounts left over 70 million users as well as their personal and financial information at risk. For a full timeline visit PlayStation Network Hack Timeline.
Because Sony had waited a full 6 days after the time of discovery to present a fully detailed announcement most people are wondering why the delay with informing the public. Typically when a breach does occur it is not uncommon for some amount of time to pass before the public is fully informed, this is usually to confirm the facts, consider solutions and prevent public panic. However during this time users could have been taking their own preventative measures by informing their credit card companies, monitoring credit reports, and avoiding phishing scams. For a great article concerning the legality of informing the public in the event of a security breach visit PlayStation Network hacked, data stolen: how badly is Sony hurt?
The PlayStation Networks Official Website released a statement detailing what efforts are being made to rectify this unfortunate situation and promises that it is a temporary issue that will be cleared up as soon as possible. Currently the network connection is still deactivated. An outside security investigation company has also been contracted to investigate the security breach and Sony is currently developing new security features. With these new features they hope resolve the system’s vulnerability and provide more safety precautions to protect a user’s personal information in the event of future occurrences.
It is PlayStations fear that the unlawful invasion into user information exposed user names, addresses, email address, birthdays, passwords, logins, purchase history, and even billing information. The official statement goes on to state that even though there is no evidence that credit card information was obtained they are not ruling out the possibility. Although many Sony officials believe that the hack was to gain notoriety as opposed to financial information they cannot be certain. As Sony continues to work around the clock to regain the confidence of its customer’s users should be taking the following actions to ensure the security and protection of their information.
What you should do!
- It is advised that if you have provided any credit card information that you contact the card company and inform them that your information may have been obtained during this event.
- It is also urged that users be mindful of email, phone, and postal scams. Sony has said that they will never contact a user to acquire credit card numbers, social security numbers, or any personal identifiable information. Often hackers will take the portions of useless information and contact you pretending to be the organization in order to obtain the rest of the information that they require.
- Monitor financial activities and credit reports. Sony has provided several links on their customer notice page that can be used to check your credit report and place alerts on your accounts. Placing alerts on your account is a great security precaution and will help protect you from other users accessing your accounts.
- Sony also advises that once the network is secure and user connection is reestablished that a user should change their login information immediately.
It’s important to remember that these kinds of incidents happen all the time and unfortunately they are the reason why we need implement more and more secure practices every day. Any fraudulent charges that do result from this incident will of course be handled by Sony. One issue left un-answered is why Sony chose to wait so long to inform its users about the potential security threat?
What do you think? Should Sony have disclosed the full details and given customers the opportunity to protect themselves sooner, or were they right to gather all the information before causing panic?
Thanks for Reading and Have a Great Day!
Dustin
ComputerFitness.com
Providing Tech Support for Businesses in Maryland

Tags: Information Security, network attack, PlayStation, PlayStation Network, Sony, user, user accounts, user protection
Posted in Information Security, Web Tips | No Comments »
Friday, March 18th, 2011
When natural disasters occur many people and groups across the world feel sympathetic to those that have to endure through the hard times. Whether it is through donations, prayer, or assisting in reconstruction, people usually come together and offer their support in one form or another. However, this of course is not always the case and where good hearted people may see an opportunity to help out there are others out there that are looking to take advantage of the situation.
 Although the Internet has greatly advanced over the past years it still remains vulnerable to cyber criminals. Even with the number of safety and security precautions established on the Internet the number of threats has nearly doubled within the last two years. Social media may be partly responsible for the growing number of threats because as the number of web users increases so does the number of these attacks. Although the Internet has greatly advanced over the past years it still remains vulnerable to cyber criminals. Even with the number of safety and security precautions established on the Internet the number of threats has nearly doubled within the last two years. Social media may be partly responsible for the growing number of threats because as the number of web users increases so does the number of these attacks.
Taking into consideration how much the Internet has evolved and the number of security features that have been implemented one thing remains the same and that is the human factor. Not all people are good and this is evident with cyber hackers, criminals, and the other individuals that only see the negative opportunity when tragedy occurs.
There are a number of ways cyber criminals take advantage of the Internet and web users. Among the most frequently used methods is phishing. These websites and emails are designed not so much to take advantage of the people impacted by a tragedy but the sympathy and compassion others express following the disaster. These sites and emails are created to make them appear as a legitimate company, meanwhile they have no connection to that company whatsoever nor do they have any intention of offering the support they are promising. Their only purpose is to gain access to your information and money. Following the devastation in Japan or any of the other natural disasters like the Indian Ocean Tsunami and Hurricane Katrina , most the time people want to help which makes them a perfect target for online scammers.
Often times it is amazing how quickly support efforts are rallied. It is shocking but not surprising that just as fast as support efforts are gathered the same is being done for fraudulent swindles. As if the catastrophe wasn’t bad enough now the people who are trying to do something to help and make a difference now have the misfortune of being mislead and cheated as well. Not only are these individuals cheated out of money but the group of people facing the tragedy is not receiving the help and support they were meant to have.
Already a number of fraudulent relief efforts have been reported and there are probably many more that are yet to be discovered. Its important to remember that there always has been and most likely always will be someone trying to profit from the kindness of someone else and not to fall victim to their attempts. Remember that these criminals seek out these opportunities and take every advantage to exploit them. Some key tips include not providing your information through email and making sure that you are doing your research before donating. If you wish to help make sure you locate a secure, legitimate and reputable organization for which to offer your support with.
Learn more by going to the links below
Current situation in Japan
CBS News, Disaster in Japan
Have a Great Day!
Dustin
ComputerFitness.com
Providing Tech Support for Businesses in Maryland

Tags: cyber, cyber criminals, Email, internet, phishing, support, tragedy, website
Posted in Information Security, Internet | No Comments »
Friday, February 25th, 2011
Wireless hotspots exist almost everywhere today. Whether you are at your favorite fast food restaurant, hotel, bar, hospital, airport, or anywhere in between you most likely have access to a wireless hotspot. These Wi-Fi resources are extremely convenient and allow users to access a network in order to complete work, check email, or just surf the net. The one thing of concern however is their susceptibility to security intrusions. Wi-Fi hotspots do not encrypt their data, consequently leaving your information vulnerable to hackers.

When utilizing a wireless hotspot it is important that you take the following necessary precautions to keep you and your information protected:
Safety over Convenience:
Although it might be tempting to sign onto any network in order to get your work done it is not the smartest or safest choice. It is advised that you try to locate secure VPN locations that require a login access key. The locations may not be as convenient as the place that enable keyless network entry but they certainly offer more safety.
Prepare your computer for unwanted exposure:
When you need to the access the Internet it might not always possible to access a hotspot that is secure, so it is important that you prepare your computer to the best of your ability. In order to prime your computer for any unwanted security intrusions you may want to try the following:
Disable your Wi-Fi settings when not using it!
When not using Wi-Fi, access your settings and turn it off. If left on your device can access hotspots that could contain threats to your personal information.
Ensure that you are utilizing an active and up-to-date firewall!
Firewalls can be enabled in the security section of your computers control panel.
Disable File and Printer Sharing!
To access your file and printer sharing settings go into your control panel, click to open the computer network and internet folder, and adjust the network and sharing menu.
Encrypt your files!
Encrypting your files can be achieved by right-clicking the folder or file that you want to encrypt, clicking Properties, clicking the General tab, and then clicking Advanced. From here select the Encrypt contents to secure data check box, and then click OK.
Leave private information at home!
Unless it is absolutely necessary, try to avoid keeping important and private information on your portable computer. If you have a desktop computer at home use it house any critical data as opposed to carrying it around where it is exposed to more risk.
Don’t forget about physical protection:
It is equally if not more important to remember that your actual computer is exposed to just as much risk as the information contained on it. Don’t leave your computer unattended where someone can access it or even worse, can take it!
These are just a few of the basic quick tips to consider when working from wireless hotspots.
Have a Great Day!
Dustin
ComputerFitness.com
Providing Tech Support for Businesses in Maryland

Tags: access, computer, file, hotspot, network, secure, Wireless, wireless hotspots
Posted in Information Security | No Comments »
Friday, December 24th, 2010
Hello, Dustin back with some useful tips to assist you in creating a strong password. How confident are you with the strength of your current passwords?
Some of the elements of a strong password may appear to be common sense but be often overlooked. Most applications, resources or tools at your disposal require password protections that should not be taken for granted regardless of the level of importance that the information offers.
Passwords are for your safety and even if the information that is being protected is not detrimental, in the hands of criminals this resource could be utilized in an effective manner. It is more than likely that if a password is required the information is important and for your eyes only. Exercise the following steps to ensure that your information is safe and sheltered from outside users with a strong password.
- The longer the better: A strong password should utilize 10 or more characters.
- Variation Matters: Mix it up! Don’t use repetitive characters or common sequences.
- Add Complexity: By adding numbers, symbols, and various upper and lower case styles will greatly increase the protection of your password.
- Take advantage of the full keyboard: Avoid using familiar character groupings or letters and numbers found in the same row (example: qwerty123). Branch out using the full keyboard and select characters that have some distance between them.
Here is a Helpful method for creating a password:
- Create or think of a saying that is familiar to you,
- Select a letter position of each word, for example the first, second or last letter in each word, use this to create a row of letters,
- Add a couple numbers that you can easily remember,
- Add a symbol if allowed,
- Select 1 or more letters and capitalize it,
Example:
| When Life Hands You Lemons Make Lemonade.
wlhylml
wlhylml491
wlhylml491!
WlHyLmL491!
Check to see how this password checks out in the Password Meter! |
Additional Tips regarding your password:
- Keeping a hard copy of your password is o.k. but make sure that it is also secure. Make sure you don’t leave a hard copy of your password out or think your being clever by keeping it under your computer keyboard or taped inside you desk drawer. The best place is locked in a safe. Also avoid giving out your password or let others see it when being typed.
- Avoid using personal information such as your birth date, your pet’s name or email account.
- Number sequences may be easy to remember, but 1234 is also easy for unwanted users to figure out as well.
- Avoid misspellings, slang, backwards or transposed spellings.
- Don’t use all the same passwords for multiple applications.
Still not sure if your password is strong enough?
Employ a password checker! When creating a password some applications visually show you how strong your password is and won’t let you proceed until it meets their specifications. However for those programs that don’t present this resource users can venture out and use secure public password checkers. Try this Password checker with your current passwords! Secure Password Checker. Also available online and as browser add-ons are password generators, but these can be hard to remember since they don’t use data that is significant to you.
For addition methods for creating a strong password check out these sites:
How to choose a good password
Passwords and Pass phrases
Did your passwords meet these standards? Hope these tips and resources will be able to assist you when creating or recreating your first line of defense.
Have a Great Day!
Dustin
ComputerFitness.com
Providing Tech Support to Businesses in Maryland (more…)

Tags: Information Security, password, passwords, strong
Posted in Desktop - Workstation, Information Security | No Comments »
Friday, December 17th, 2010
 10 Tips to Help Keep Your Data Protected 10 Tips to Help Keep Your Data Protected
Hey everyone I’m Dustin, welcome back to our blog.
Worried about your information going out across the World Wide Web, continue reading to learn how you can get protected against loss of data, data theft, and data corruption.
- Physical Protection: Passwords, firewalls, and virus scanning are great but please don’t forget the basics. Keep your computer physically locked up or only leave it where you know for a fact that it will be safe. Even people you know can access your computer and bring unwanted problems if you give them the chance. Devices like security cables and alarms can be used but are not full proof. Making a note of the computer’s serial number can also be helpful if a theft does occur and needs to be reported. (Computer Protection Devices)
- Don’t be naïve not everyone is nice: Don’t give out your personal information to people you don’t know, it’s not a normal for strangers to ask for your address or birthday when you first meet them. Don’t provide too much information to social networking sites.
- Use Antivirus and Spyware programs: Using good Antivirus software is not enough anymore. New malicious programs are created and discovered every day so it is important that you not only have Antivirus software but that you keep it up to date as well. Antivirus programs scan, track, and remove any problems from your hard drive. Like Antivirus software a spyware program can detect and eliminate any spyware that has made a home on your hard drive. Many Antivirus programs do have anti-Spyware included, if yours does not, you will need to install a separate program for Spyware. Spyware can often track your web usage, violate your privacy, add unwanted features, and take up your computer usage for its own purpose. (Learn More)
- Back up your information: If you don’t already have a back up of your hard drive you should create one. Sooner or later you may encounter a problem that requires a complete hard drive wipe so avoid the hassle of re-building your information and create a backup. There are many programs that will automatically create a back up for you some of them programs include Symantec Backup Exec, Ace Backup, Nero Back it up, Save Me PC, and Evault. Chances are that if you have a security or antivirus program on your computer they will establish a hard drive back up already on a routine basis.
- Activate your Firewall: To make certain that your firewall (in Windows) is active access the control panel, go to network and connections, and select firewall settings. Additional programs like Norton Security Suite and McAfee Security provide additional firewall settings. A firewall acts as a barrier between the internet and your computer protecting it from outside access and intrusive problems. Firewalls are essential to controlling the traffic through the various network ports.
- Learn and Beware: Educate yourself, don’t be fooled, and take a closer look to see what information is accurate and safe. Avoid pop-ups asking you to install software, only install free software that you are sure about and no is safe. Don’t open attachments without scanning first and don’t open links in your emails that you suspect might be bogus.
- Avoid Phishing: Phishing is when emails falsely claim to be an existing organization that you do business with. These emails redirect a user to a website created to look like the legitimate site and then users are asked to update their personal information. Mean while the real company has no need of asking for updated information and you just supplied it all to a criminal. Be cautious of emails expressing urgency and avoid links and submission forms asking for financial information. Sensitive information like this should only be communicated using a secure webpage. (More about protecting yourself against phishing!)
- Make sure pages are secure: Whether it is to purchase items, check bank accounts, or to logon to other sensitive information be certain that site is displaying a security icon on the browser window. In addition to the locked icon, an encrypted web site URL will include https instead of the unencrypted http. Depending on the web browser that you are using the icon will be located in various locations. Take the time to familiarize yourself, knowing where yours is located could prove to be very beneficial. If using Internet Explorer the icon is located next to the search dialogue box at the top right and in Mozilla Firefox it is located in the lower left hand page border. Clicking this icon will launch a separate window detailing the security properties of the webpage. (How to tell if the Page is Secure)
- Create strong passwords: A password should be easy for you to remember and hard for others to figure out. A strong password should be 10 to 14 characters in length. The longer the better but only if you’re able to remember it. Avoid any password based on repetition, dictionary words, letter or number sequences, usernames, relative or pet names, romantic links (current or past), or biographical information (e.g., dates, ID numbers, ancestors names or dates). A password should include numbers, and symbols if allowed by the system. If the system recognizes case, use both capital and lower-case letters. On another note about passwords don’t leave them out where people can see them. A strong password is nothing if you leave a hard copy of it under the keyboard, taped to the desk, or even worst attached to the monitor. Hard copies should be kept in a digital wallet or safe. Also switch it up don’t use the same password for everything. If someone can get into your email that is bad enough you don’t want to give them access to your bank information also. An addition authentication tip is to confirm your user account does not have administrative access on your computer. If for example you are a regular user and despite having anti-Malware software installed, some malicious software gets through, the malware software would only be able to affect your profile and not your computer’s operating system as regular users cannot install most software. (How to Create and Strong Password)
- Wi-Fi Settings: When using public or personal Wi-Fi, be sure to turn off file sharing (Windows) by going to your control panel, selecting network and connection, tab to advanced settings and adjust accordingly. In addition you can activate privacy settings and change the firewall configurations in the same location. Make sure that you have an active firewall and ensure that you turn off the Wi-Fi when no longer using it. It’s also worth mentioning that users should always have their home Wi-Fi connections encrypted so users can’t stand around your house and access it. Also make sure no one is hovering to get your login password.
Hope these tips can help! It is only by taking preventative measures like these that we are able to hopefully stay ahead of cyber crime.
Keep your information Safe and Have a Great Day!
Dustin
ComputerFitness.com
Providing Tech Support to Businesses in Maryland

Tags: Firewall, Information Security, Software, strong password
Posted in Information Security, Mac and PC, PC, PC Maintenance | No Comments »
Friday, October 29th, 2010
 Hey, everyone, Josh from Computer Fitness back with another award-winning article to help you with your computer conundrums. Hey, everyone, Josh from Computer Fitness back with another award-winning article to help you with your computer conundrums.
Recently, another glitch in the iPhone’s security was found. When you lock the screen, there is a chance for people to gain access to your system, despite having a lock in place. It involves using the Emergency Call function, and a few quick button presses. This is concerning for many people, and Apple has yet to address it. There are rumors that it will be fixed in the upcoming software update, 4.2, but we aren’t sure yet.
Keeping your mobile device safe is important. The amount of data on it is vital to your business, personal life, or both. This is why proper security measures are so important. No matter which device you use, always password protect them. Whether it is a PIN or a 32 Digit masterpiece of a lock, make sure you take the right steps.
Tied into this is keeping passwords up to date and changing them as necessary. For example, if you set up your iPhone for SSH, which allows file transfers, etc., then you want to change the default password from “alpine” to whatever else. The same goes for routers and wireless networks. Always setup encryption, no matter how simple. A WEP goes a long way to keep people from stealing your data on your home wireless network.
Remember, you’re the best line of defense against digital attackers. You don’t have to be a specialist, but you do need to take the initiative.
Josh

Tags: Apple, Information Security, microsoft, Networking, passwords
Posted in Information Security | No Comments »
Friday, October 15th, 2010
 Hey, everyone, Josh from Computer Fitness back with another award-winning article to help you with your computer conundrums. Hey, everyone, Josh from Computer Fitness back with another award-winning article to help you with your computer conundrums.
We all want to protect our PCs. After all, a multitude of threats exist. We need to squash them before they even get to our door. But how do we do this? The gut reaction might be to implement as much protection software as possible. However, this is not the case. In fact, if you start stacking protection software you are setting yourself up for future PC woes.
It used to be the case where you had anti-virus software as well as malware protection and even a firewall. They were all separate programs from different companies. Today, and for the past several years, companies are creating all in one solution for your security. This means you can pay one fee and have all of your bases covered.
Remember that keeping your PC safe means also keeping it from getting bloated with old software. Always be careful about what you install.
-Josh
Computer Fitness

Tags: Malware, pc, protection, Software, Viruses
Posted in Information Security | No Comments »
Wednesday, September 1st, 2010
 Hey, everyone, welcome back to the Computer Fitness blog! Hey, everyone, welcome back to the Computer Fitness blog!
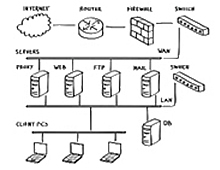
Keeping your data safe and secure is a necessity in any business. Clients don’t want their private information being leaked all over the world, and who can blame them? We all want to make sure our privacy is protected at work and at home. Well, there are a lot of ways to ensure that you remain safe on the web. Today, we’re going to talk about one of them: Firewalls.
Picture a wall in your head. Now cover it in fire. That’s effective imagery, right? You wouldn’t be able to go anywhere near it. That’s the aim of firewalls on computers. They act as barriers to prevent people from just coming in and getting what they want. They are meant to establish lines so thick that nothing can penetrate them.
Getting a firewall is easy. All Windows and Mac operating systems have them built- in. They are also usually enabled by default. This is good because it keeps you from having to configure this yourself. They automatically block most ports you won’t use, and keep open ones that you will. A good example is port 80, which is the default for web browsing. That will be open, while others will not.
There are other forms of firewalls you can employ, and all have varying degrees of strength and customizability. For a home user, any good Anti-Virus bundle will include a more powerful firewall that is better equipped to handle your PC’s security.
-Josh
Computer Fitness

Tags: Firewall, Information Security, mac, pc, WWW
Posted in Firewall, Information Security | No Comments »
Thursday, August 12th, 2010
 Hey, everyone, Josh from Computer Fitness yet again. We are a Tech Support Company for Small and Medium businesses located in Reisterstown, MD. Hey, everyone, Josh from Computer Fitness yet again. We are a Tech Support Company for Small and Medium businesses located in Reisterstown, MD.
Protecting your PC is an important part of ownership. Just as you would buy a security system for your car, you must also acquire security for your computer. There are a plethora of options out there. You can choose from open source free programs to powerhouse software created by giant corporations. The latter is probably your best option if you don’t feel like spending hours learning how to use the software.
Symantec
Probably one of the best known protection suites, Symantec’s Norton Internet Security suite has been a household name for a while. It provides protection for up to 3 PC’s per household and covers a lot of areas. The reason I recommend this over the cheaper, Antivirus Edition, is because there are more than just viruses seeking to cripple your PC. On top of this, features like cloud-based definitions for threats and child protection while online are worth having.
McAfee
McAfee has been around for a while, too, and so they also have a respectable history. Their product is very similar to Symantec, and even Trend Micro. Features such as antivirus defense, firewalls, etc. are all present here. The biggest difference here is the lack of home network protection. This is included, in some form or another, in both Symantec and Trend Micro. Its absence here is notable.
Trend Micro
Trend Micro is, in my opinion, the best option out there today. While sporting similar features to its competition, Trend Micro stands out for its offer of 2GB of free online storage, quick scan times, and real time change tracking. These last options informs you the second attempt are made to change something on your PC. This is handy when installing programs and making sure they do what they say they will. On top of all this is an interface that is easy to use.
-Josh
Computer Fitness

Tags: Antimalware, Antivirus, Information Security, Malware, pc, Spyware
Posted in Information Security | No Comments »
|












 Hey, everyone, Josh from
Hey, everyone, Josh from  Hey, everyone, welcome back to the
Hey, everyone, welcome back to the  Hey, everyone, Josh from Computer Fitness yet again. We are a Tech Support Company for Small and Medium businesses located in
Hey, everyone, Josh from Computer Fitness yet again. We are a Tech Support Company for Small and Medium businesses located in 

